AllSafe
Safeguard Your Future
Stay Ahead with Total Cybersecurity Protection
Security Solutions Trusted by Leaders





Secure Your
Business,
Defend
Everything
Ultimate Cyber Protection
And Digital Security Solutions
Advanced Solutions for Ultimate Cybersecurity Defense
Experience True Security

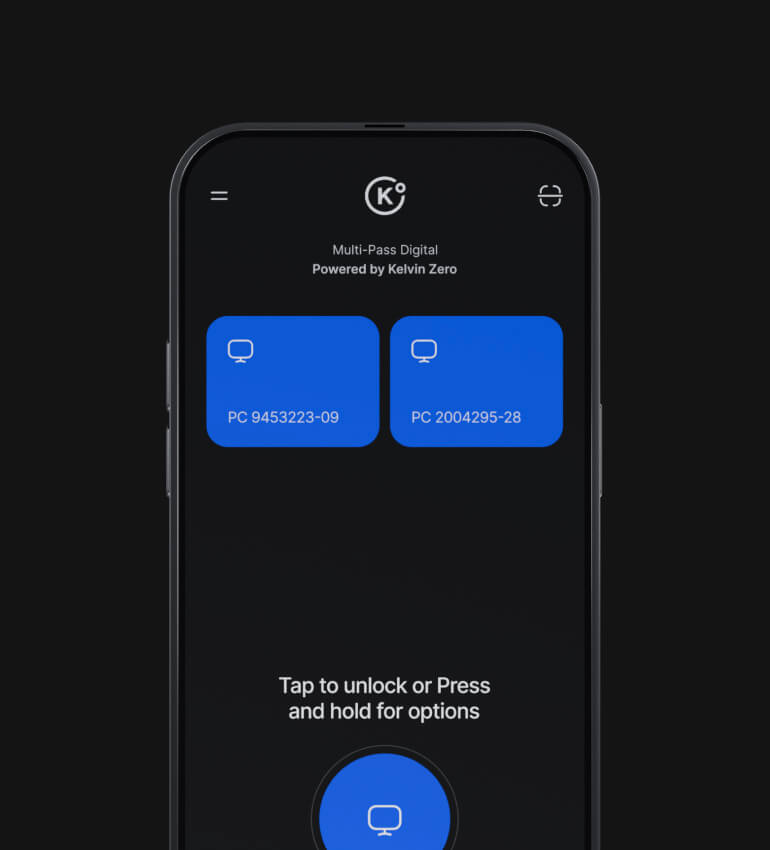
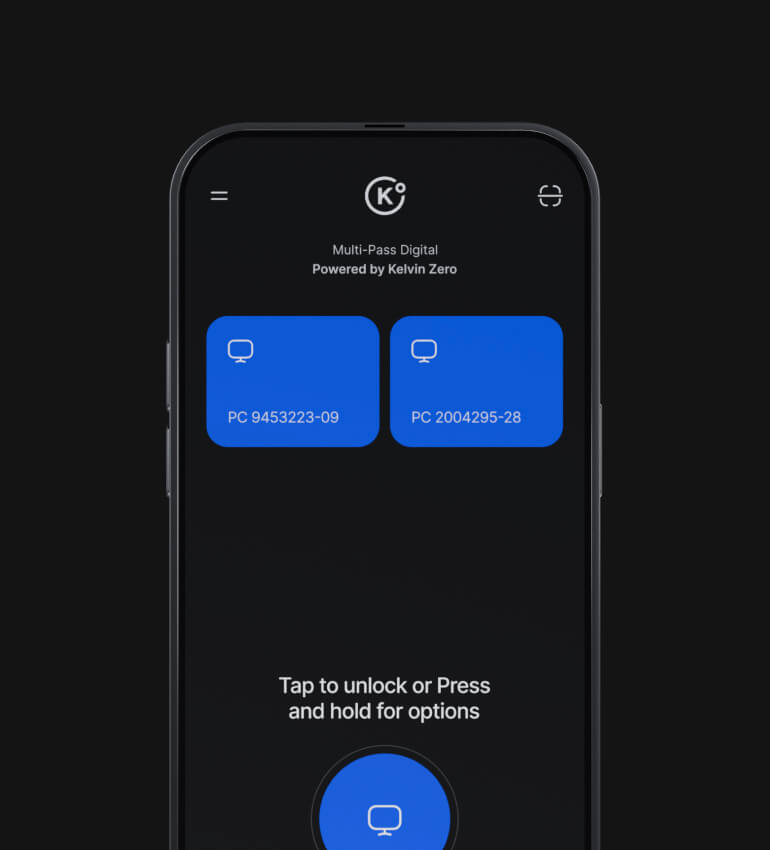
Deliver a secure and frictionless login experience

Meet and exceed stringent regulatory requirements

Reduce costs and free up IT resources

Future proof against new credential-based threats
Comprehensive Cybersecurity for Business Continuity

Fortify your organization’s digital defenses with cutting-edge, enterprise-grade security solutions designed to combat emerging cyber threats.
Advanced Threat Monitoring
Multi-Layered Security
Real-Time Cyber Intelligence
Proactive Threat Hunting
Stay ahead of attackers with proactive threat detection and response, leveraging advanced machine learning and behavioral analysis.
Next-Generation Endpoint Security
Deploy state-of-the-art AI-driven solutions to safeguard critical systems from sophisticated cyber attacks.
Strengthen your defenses with adaptive security measures that evolve with emerging threats.



Security Architecture Design & Implementation
The Power of Secure Element Technology
We craft robust security architectures tailored to your unique needs, incorporating advanced firewalls, intrusion detection/prevention systems (IDS/IPS), and security information and event management (SIEM) systems to protect your environment.

24/7 Threat Monitoring & Incident Response
Our team provides around-the-clock monitoring to detect and neutralize threats in real-time. In the event of an incident, our rapid response experts are on standby to contain and resolve the situation swiftly and effectively.

Vulnerability Management & Patching
Keeping your systems up to date is crucial in preventing exploitation. We perform continuous vulnerability assessments, apply necessary patches, and implement best practices to ensure your infrastructure remains secure.

Endpoint Security Solutions
Protecting every device connected to your network is essential. We deploy cutting-edge endpoint protection tools that secure workstations, mobile devices, and all endpoints against malware, ransomware, and other cyber threats.
Integrate with your existing IdP and enable easy access to all your company resources
Workstation
Logins
Web Services
& Apps
Remote Work
Access
Physical
Access
Custom &
Legacy
Frequently Asked Questions on Cybersecurity
Encryption is the process of converting information or data into a code, especially to prevent unauthorized access. It's crucial for protecting sensitive data, ensuring that even if data is intercepted, it cannot be read without the decryption key. Encryption is used in various forms such as securing communications, protecting files, and securing online transactions.
To prevent malware, it's important to regularly update your software, use reliable antivirus solutions, and avoid clicking on suspicious links or downloading unknown files. Additionally, educating employees on phishing schemes and using firewalls and intrusion detection systems can greatly reduce the risk of malware attacks.
To protect against phishing, ensure your employees are trained to recognize suspicious emails or messages. Implement multi-factor authentication (MFA), use email filtering solutions, and conduct regular security awareness training. Phishing simulations can also help test and improve your organization's preparedness.
A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It helps block unauthorized access to or from a private network, providing a barrier against external cyber threats while allowing legitimate communication to pass through.
Protecting sensitive data involves implementing data encryption, enforcing access controls, using data loss prevention (DLP) tools, and conducting regular audits. Additionally, ensuring compliance with security regulations like GDPR or HIPAA, and educating staff about data privacy best practices is key to safeguarding sensitive information.
Ready to go?
Schedule a Demo
Join Kelvin Zero
Help us create a safer digital world for everyone
We are growing fast and are looking for like-minded and ambitious people to join our team of world-class entrepreneurs and cybersecurity experts.